Create firewall rules using PowerShell New-NetFirewallRule
You’ve probably searched and found some guides that tell you to use PowerShell to create firewall rules for Teams.
You can now use an Endpoint security policy to create firewall rules for Teams installed in the user profile %localappdata%\Microsoft\Teams\current\Teams.exewhich is much simpler than trying to deploy a PowerShell script to modify per user firewall rules for Teams.
Windows Defender Firewall prompt for Teams
The first time you open Teams, you'll get this prompt to allow Teams through the firewall. Allowing Teams through the firewall requires admin rights.
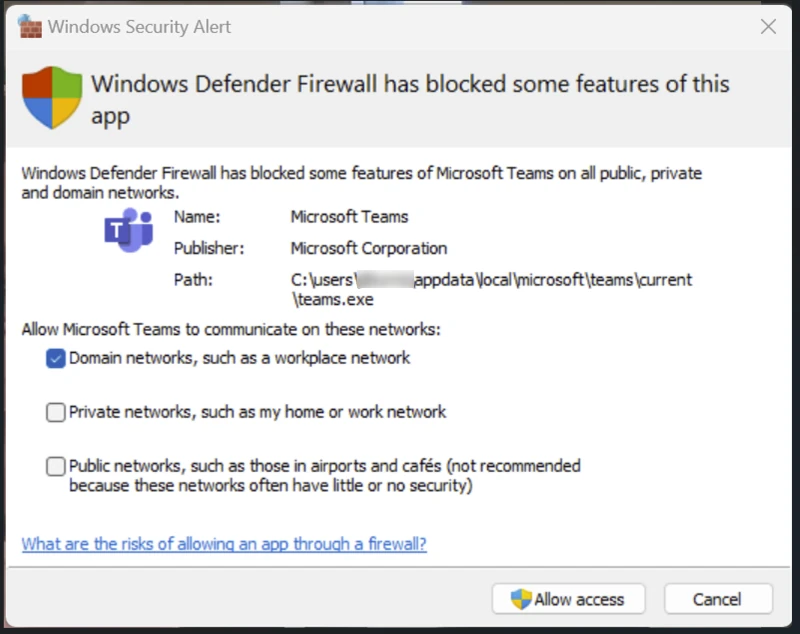
To make this more user friendly and to avoid having to enter admin credentials the first time Teams is launched, we’ll create Endpoint security policy to allow Teams through the Windows Firewall
Create Endpoint security Firewall policy
Intune admin center
Endpoint security - Firewall - Create policy
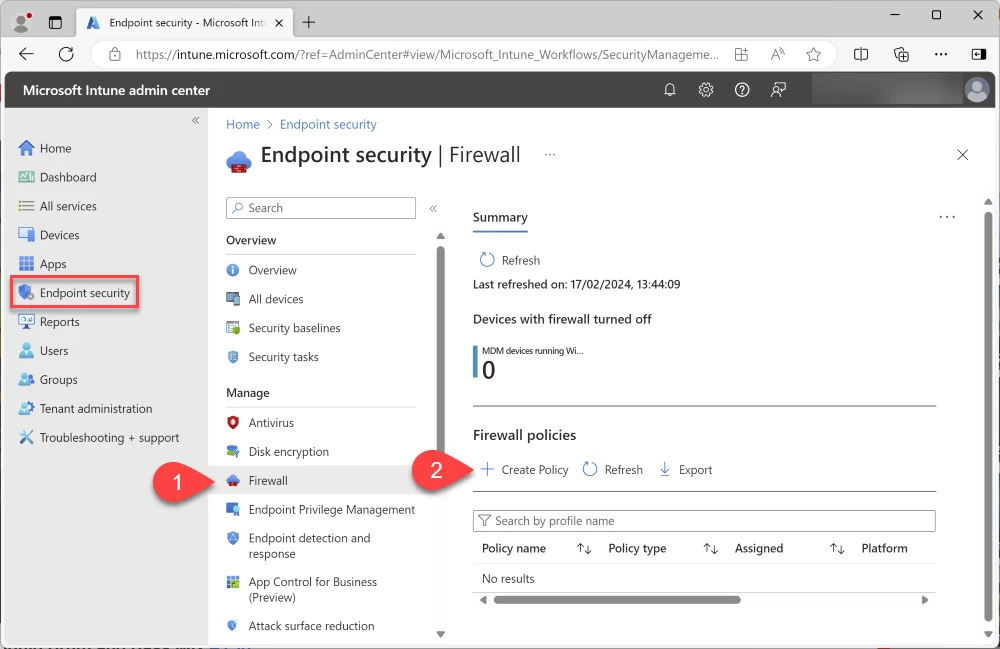
Create a profile
Platform: Windows 10, Windows 11, and Windows Server
Profile: Windows Firewall Rules
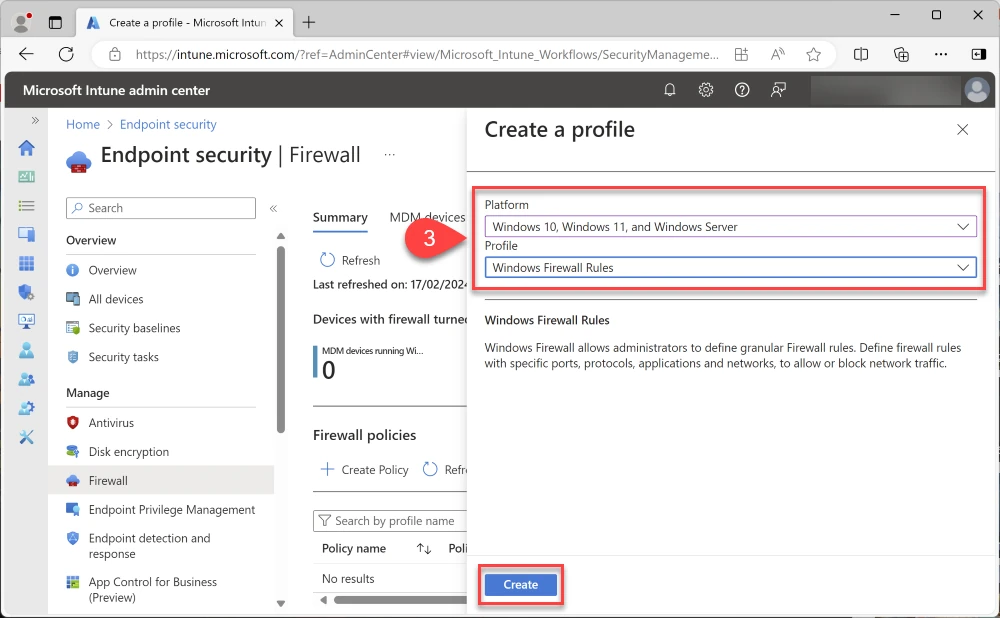
Name: Windows 11 Firewall Rules
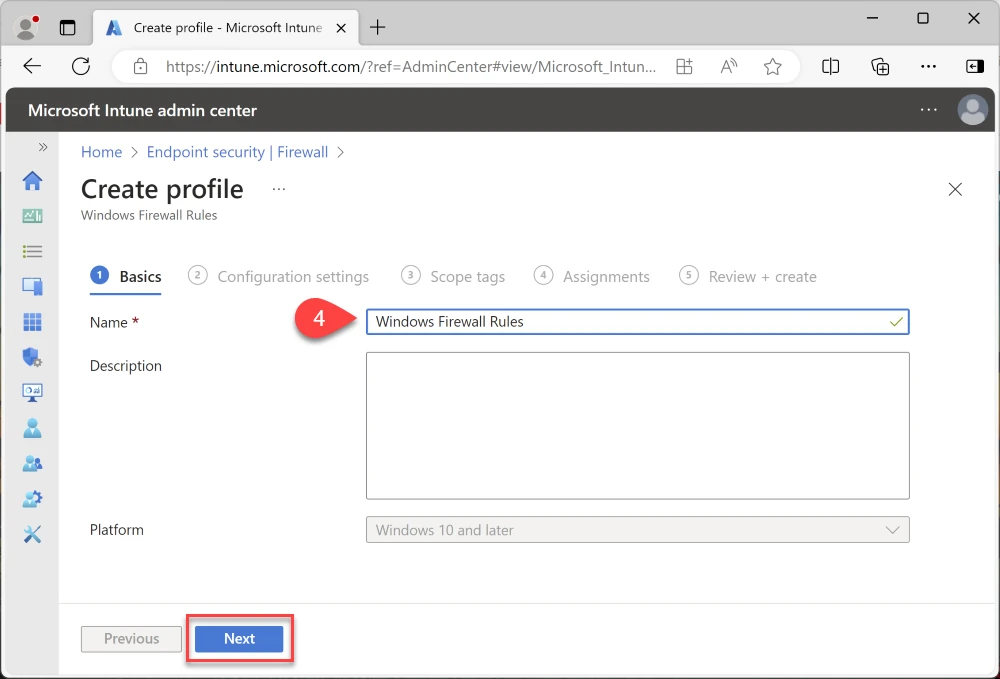
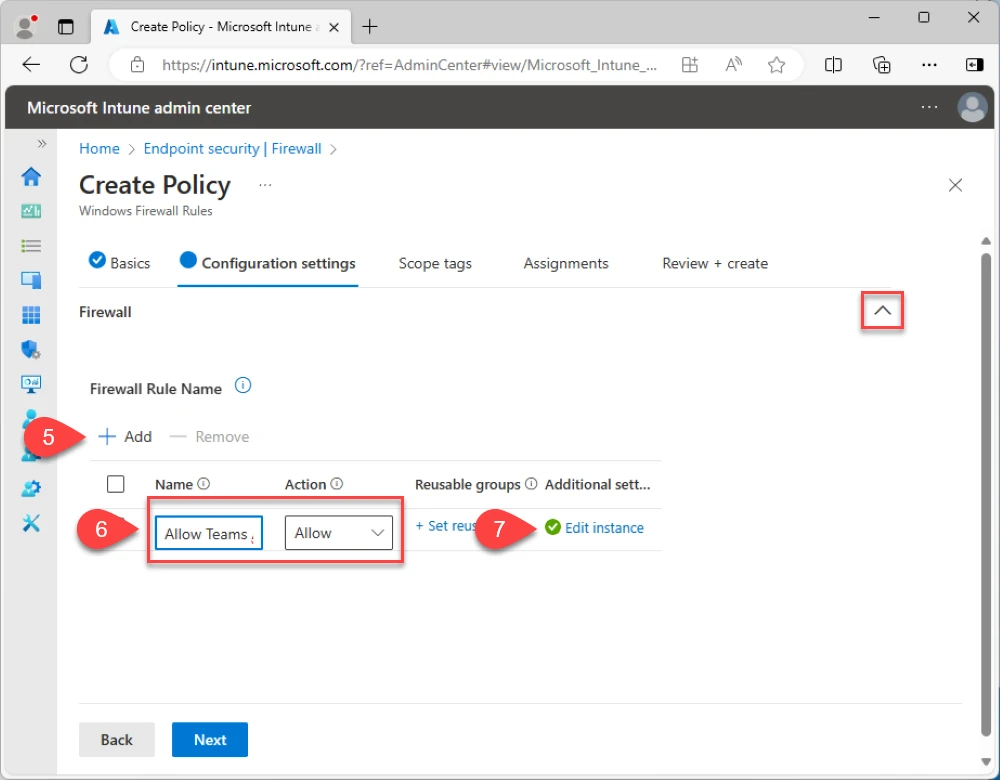
Expand Firewall - Add Firewall rule
Name: Allow Teams AppData Local
Action: Allow
Edit instance
Policy Settings
Enabled
Name: Allow Teams AppData Local
File Path: Configured
Teams user profile installer file path
%localappdata%\Microsoft\Teams\current\Teams.exe
Teams machine wide installer file path
C:\Program Files (x86)\Microsoft\Teams\current\teams.exe
Direction: The rule applies to inbound traffic
Leave other settings as the defaults
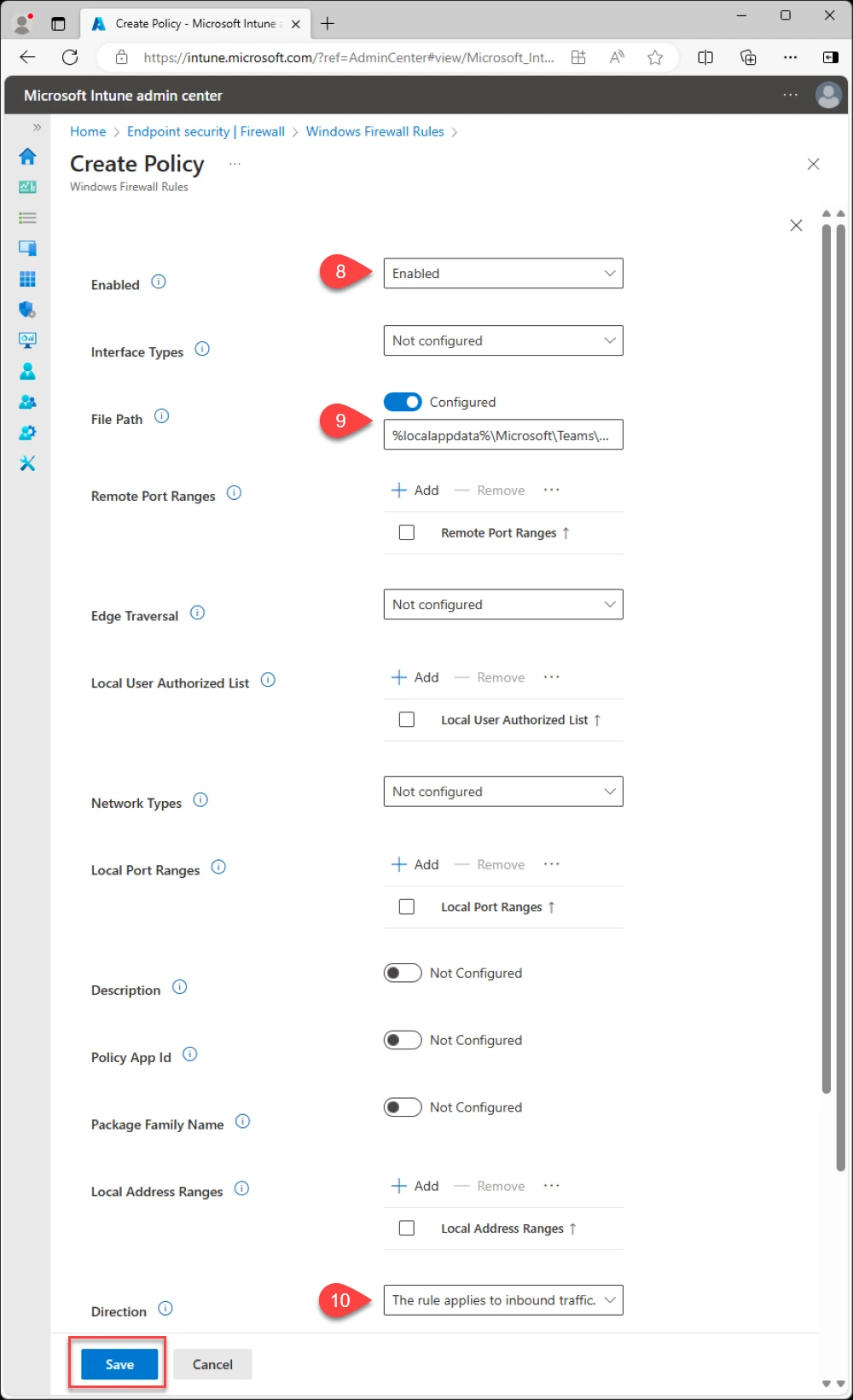
Click Next
We're not using scope tags, click Next
Assign the policy to a test group
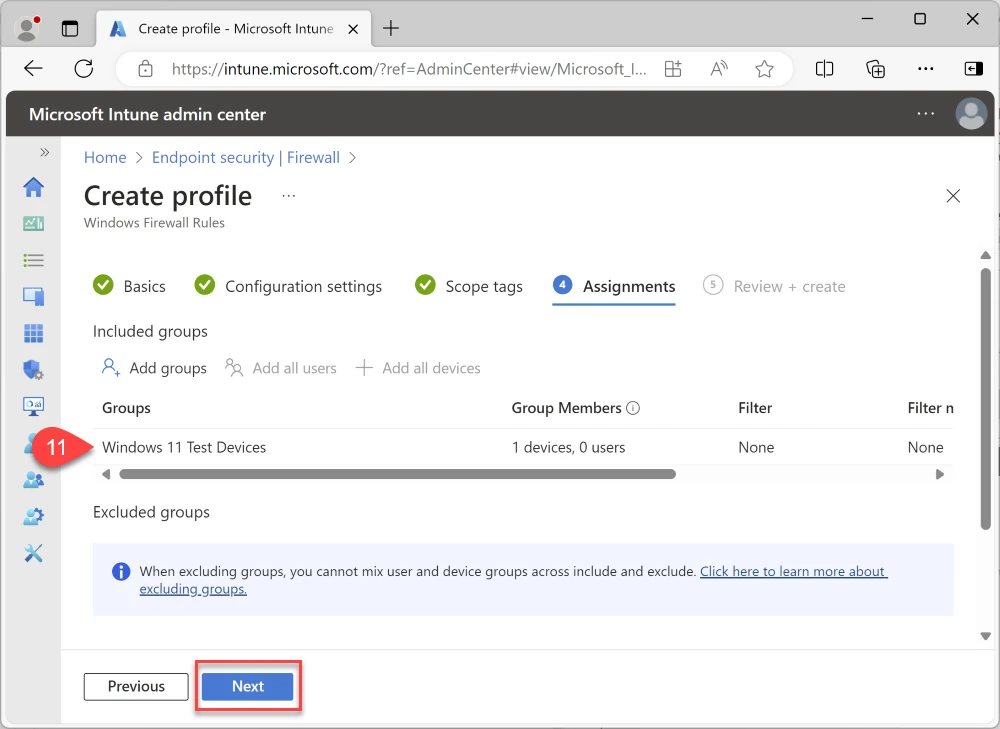
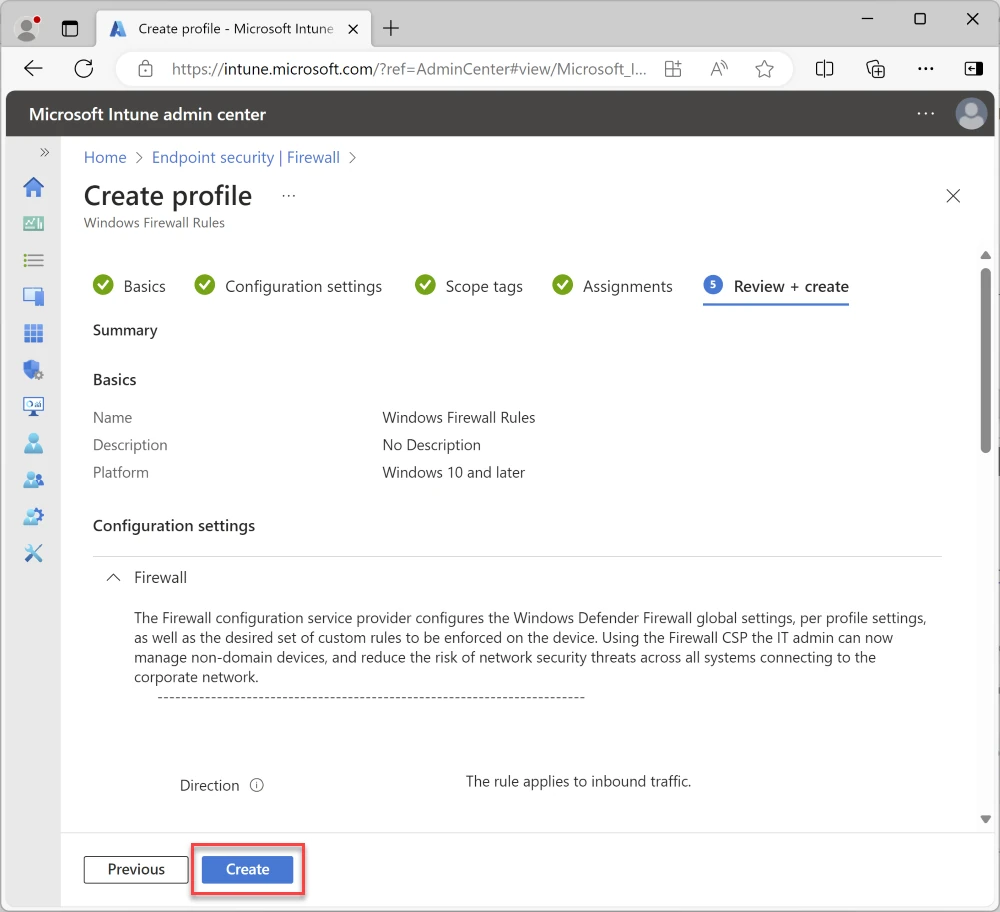
Click Create
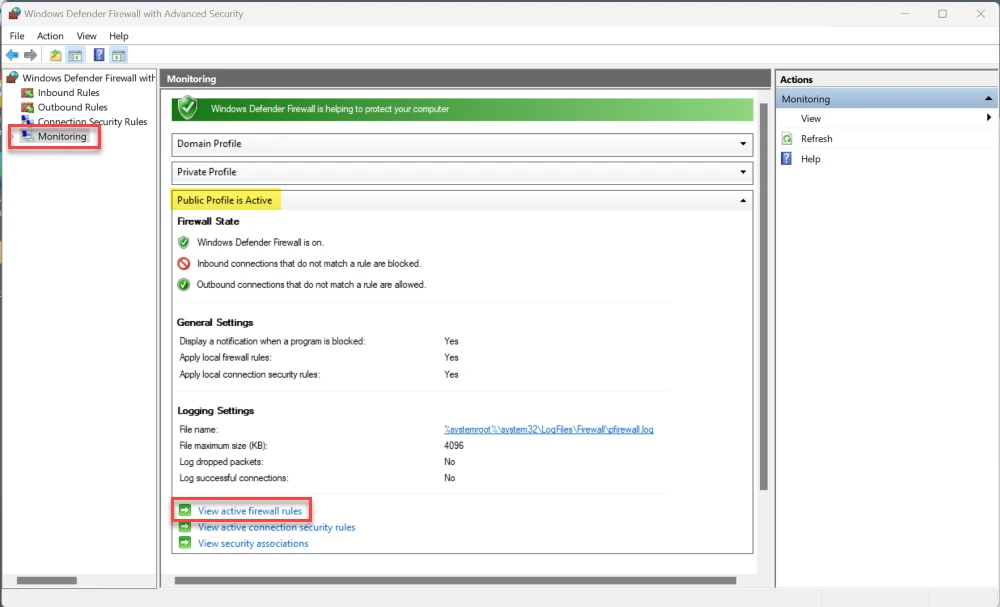
View Endpoint security firewall rules in Control Panel
Control Panel - Windows Defender Firewall
Advanced Settings - Monitoring - Select Firewall Profile e.g. Public
View active firewall rules
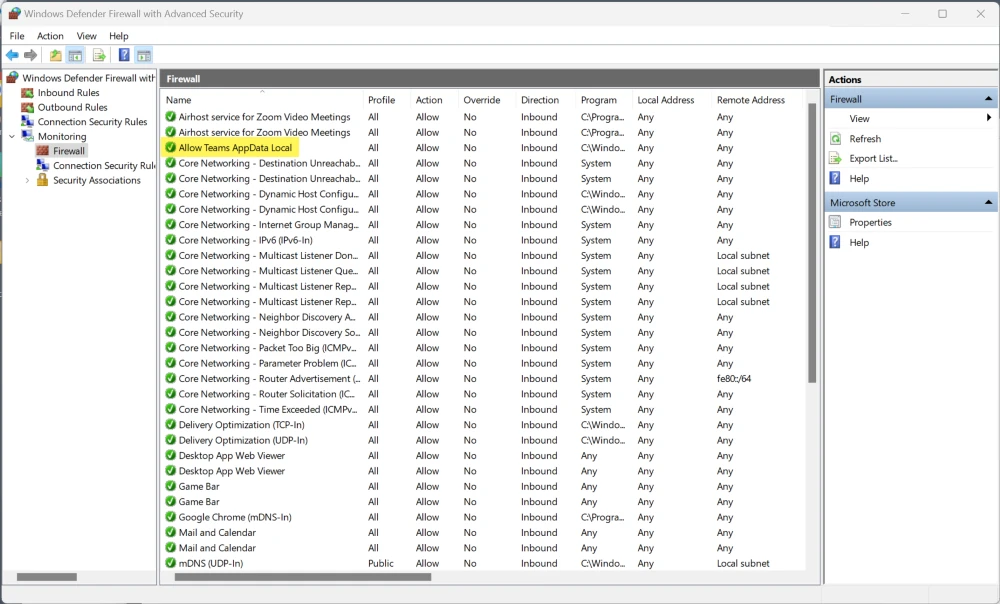
The "Allow Teams AppData Local" Windows firewall rule has been created
Subscribe
Report